ENTERPRISE APPLICATION ACCESS
Application Access Redefined: Secure, Simple, Fast.
Displace Traditional VPNs
Traditional VPNs are complex to manage and expensive to scale. Eliminate the operational cost and risk involved in maintaining and patching VPNs and other appliance-based solutions for scalable, secure application access.
Secure Access to Cloud Applications
Migrating on-premises applications to IaaS providers can be challenging. Leverage the power of multiple clouds by enabling secure access to applications across AWS, Azure, and Google Cloud.
Logging
Efficient and swift integration are imperative to M&A success. Accelerate the pace of mergers and acquisitions by enabling shared access to applications, without complex or costly network consolidation or re- architecture.
Secure Remote and Third-Party Application Access
Reduce the risk of compromise from remote employees, third-party contractors, partners, and mobile users — regardless of their location — by delivering secure application access without the need for network access.
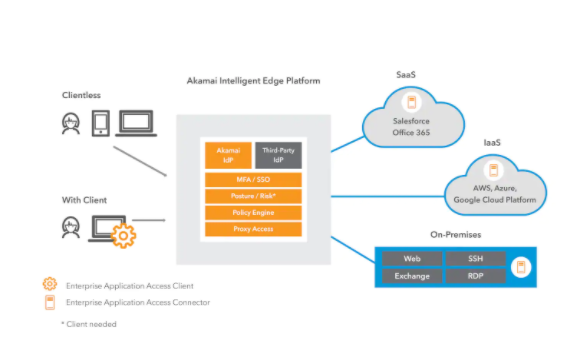
How Does Enterprise Application Access Work?
An Enterprise Application Access connector connects to your application server, then dials out to the Enterprise Application Access service on TCP port 443, commonly open for outbound communication on most companies’ firewalls. No additional hardware or software is required.
The service is architected based on three primary components:
- Data Edge: Provides the data plane between the user and the application, as well as data security, application performance, and optimization components.
- Management Edge: Provides management, logging, reporting, and configuration capabilities. The management and data edges are based on a secure, multi-tenant architecture. In addition to the multi-tenant data cloud, you have the option to select a dedicated single-tenant data cloud that can be configured to only process a single user’s traffic.
- Enterprise Connectors: Users connect to the Enterprise Application Access single sign-on service through a URL entered into their browsers. They simply provide their credentials to gain access to applications. Enterprise Application Access can also integrate with existing SSO products. Akamai’s solution captures information such as user identity and contextual signals, as well as device posture, meaning device vulnerability and threat intelligence signals, to build out robust risk profiles that assist with secure access decision-making.
Enterprise Application Access works with all applications — legacy on-premises, IaaS, and SaaS.
BENEFITS TO YOUR BUSINESS

Enable Business Continuity for All Users
Deliver secure access to your business-critical applications for all users, regardless of location and application type— without the need for full network access.

Leverage an Enterprise-Level Secure Access Platform
Implement an enterprise-grade solution with IdP, MFA, and SSO capabilities, as well as load balancing and end-to-end encryption.

Reduce Technical Complexity and Debt
Leverage a user/application-centric model for secure access by building on the unmatched scalability of the Akamai Intelligent Edge Platform.

Enhance Access Decisions Using Multiple Threat Signals
Leverage threat signals from users, devices, and third-party applications for more granular, more secure decision-making.
